Advanced Threat Protection
Detect and Block Access to Malicious Entities
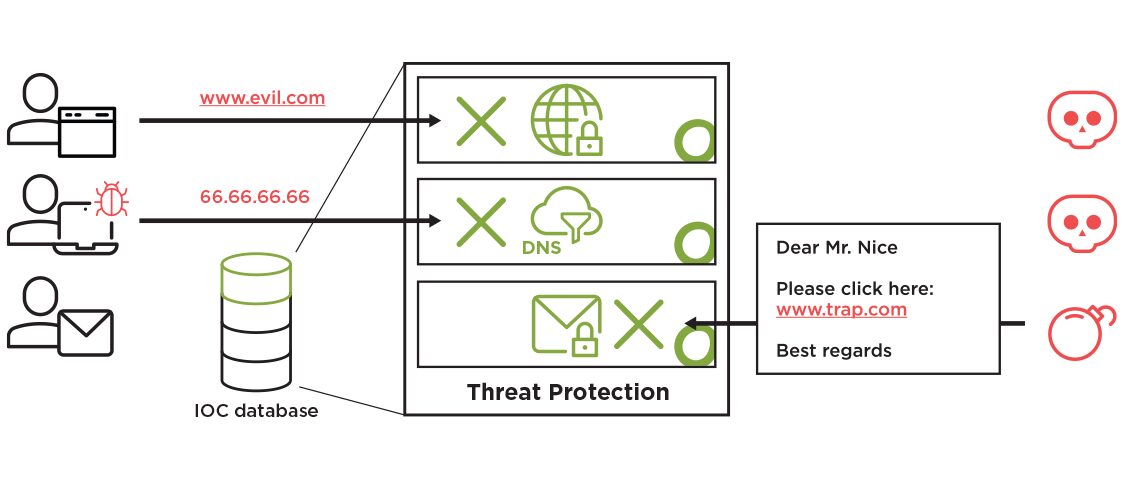
Advanced Threat Protection from Open Systems blocks malicious URLs, domains, and IPs. It aggregates different threat intelligence feeds – delivering known indicators of compromise (IOCs) in real time.
Advanced Threat Protection (ATP) offers enhanced defense of your important data by adding more protection layers and high quality, commercial intelligence feeds for zero-day threats.
Unified Threat Intelligence for
Web and Email Security
Quickly Catch Threats
Commercial threat intelligence feeds designed specifically to catch zero-day threats quickly.
High Quality Threat Intelligence
Third-party databases and feeds deliver verified malicious URLs, domains, and IP addresses in real time.
Threat Intelligence Management
Our engineers curate the used threat intelligence feeds resulting in a first-class set of feeds covering different attack vectors.
Commercial Threat Intelligence for
Zero-Day, High Quality Protection
Advanced Threat Protection offers additional, enterprise-grade zero-day threat intelligence feeds from leading security solution providers, as an add-on to the basic Threat Protection, which is included in our Secure Web Gateway, DNS Filter and Secure Email Gateway solutions. These feeds combine information from various sources to classify the URLs and domains.
- In-house spam traps and honey pots
- Hosting companies and registries
- Law enforcement and internet governing bodies
- Enterprise businesses and internet service providers
- Independent security researchers and volunteers
How It Works
High Quality and Zero-Hour Threat Intelligence Feeds Through Active IOC Feed Management
- Always the latest and greatest IOC information
- Including zero-day or even zero-hour/zero-minute IOCs
- Automatically updated in the central IOC database for real-time protection
- Granular, specific threat information in the form of URLs instead of IPs/domains
- Diverse sourcing of IOCs: email vendors and MTAs, DNS servers, ISPs, security community, etc.
- Very low false-positive rate even for quickly changing threats
- Regular, automated, and human reviews of IOCs
- Reporting functionality and 24×7 support
Fast
Specific
Reliable
- Always the latest and greatest IOC information
- Including zero-day or even zero-hour/zero-minute IOCs
- Automatically updated in the central IOC database for real-time protection
- Granular, specific threat information in the form of URLs instead of IPs/domains
- Diverse sourcing of IOCs: email vendors and MTAs, DNS servers, ISPs, security community, etc.
- Very low false-positive rate even for quickly changing threats
- Regular, automated, and human reviews of IOCs
- Reporting functionality and 24×7 support
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us