
ZTNA
Provide Secure Access to Anyone Anywhere
What is ZTNA?
ZTNA stands for Zero Trust Network Access which is a security framework that shifts the focus from traditional perimeter-based security to a more holistic approach, where every user, device, and network connection is treated as untrusted by default. The main principle of ZTNA is “never trust, always verify,” which means that each access request must be authenticated, authorized, and continuously validated before granting access to resources or data.
Zero Trust Network Access architecture follows an adaptive trust model, operating on a need-to-know, least-privilege basis.
Under ZTNA, only authenticated and authorized users, endpoints, and applications are granted access to corporate resources. Access is centrally managed, policy-based, and granular, ensuring flexibility and security.
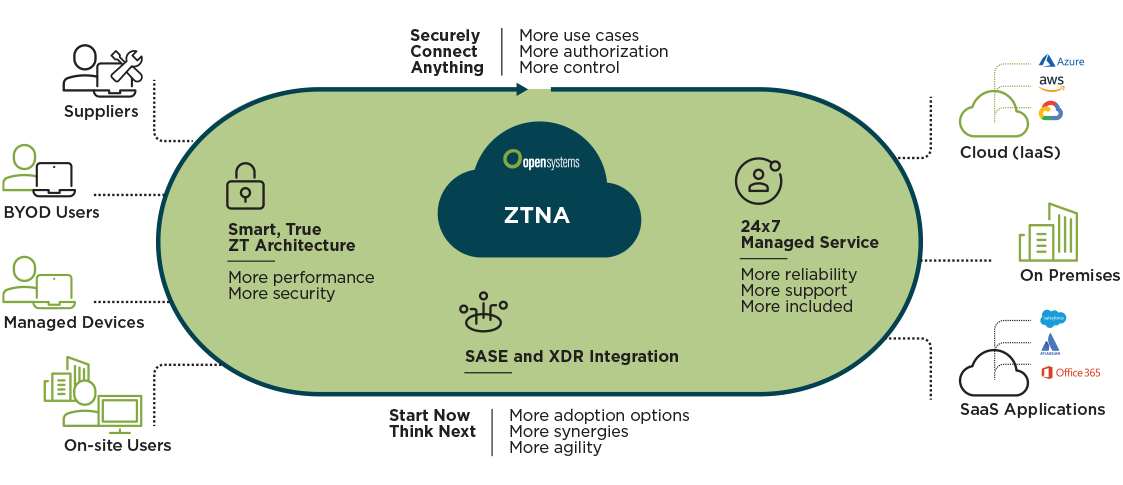
Why organizations need ZTNA
Connect Everything Securely
ZTNA provides flexible and secure access to users, sites, and partners using any device, anywhere in the world.
ZTNA Cloud
We offer integrated, smart routing via cloud-based ZTNA PoPs, ensuring higher performance.
True Zero Trust Architecture
By separating identity provider, traffic routing and ZTNA, the impact of a compromise can be minimized.
24x7 Fully Managed Service
Our ZTNA is delivered with all the required capabilities and functionalities to start using it today.
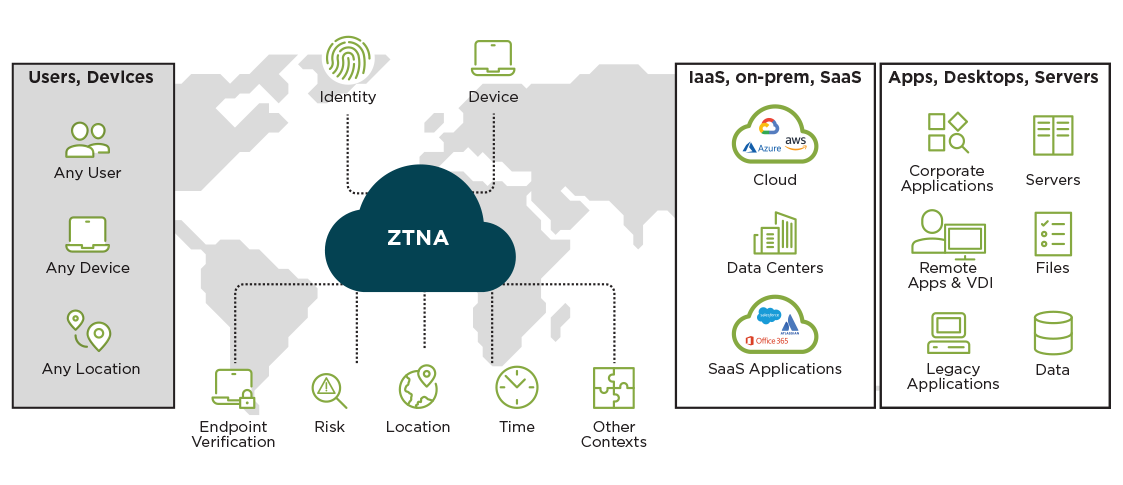
How ZTNA Works
- Agentless or agent-based to include any type of user
- For agent-based: enforce encryption on all incoming traffic via ZTNA by adding a Secure Web Gateway
- Enrich authentication using credentials, certificates, and MFA
- Set policy by factors including user group, device posture, and XDR-provided risk score
- Ensure short paths and place enforcement points near your apps
- Control access to corporate SaaS, cloud-based and on-premises applications
Serve Every User
A Range of Policy Options
Access All Applications
- Agentless or agent-based to include any type of user
- For agent-based: enforce encryption on all incoming traffic via ZTNA by adding a Secure Web Gateway
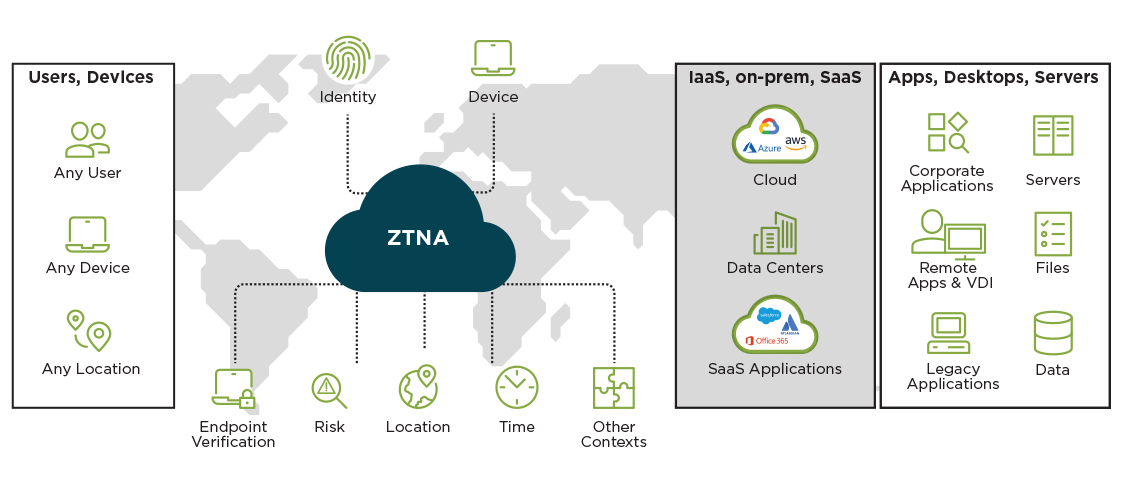
- Enrich authentication using credentials, certificates, and MFA
- Set policy by factors including user group, device posture, and XDR-provided risk score
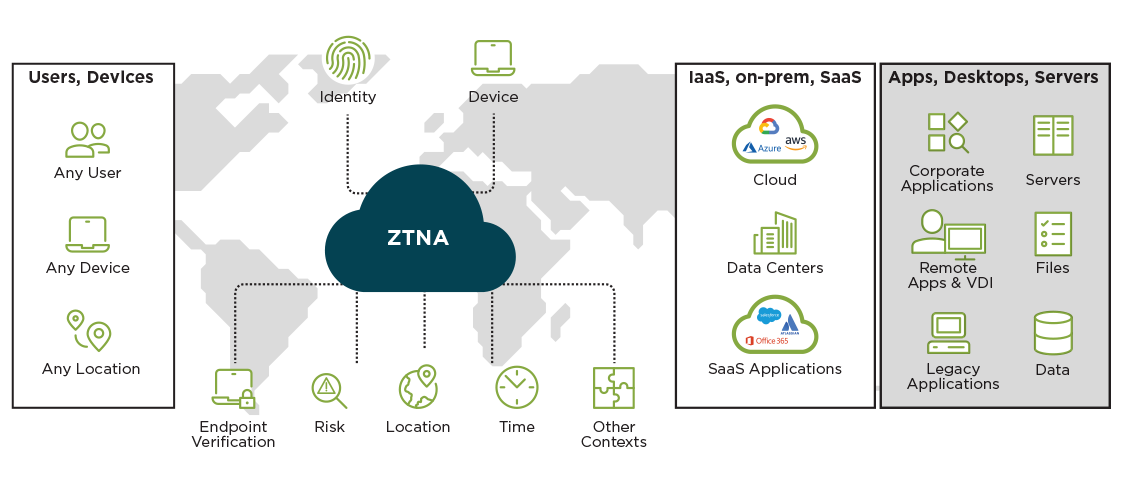
- Ensure short paths and place enforcement points near your apps
- Control access to corporate SaaS, cloud-based and on-premises applications
ZTNA vs. VPN
ZTNA and VPNs (Virtual Private Networks) are both technologies that enable secure remote access to organizational resources. However, they differ in their approach, architecture, and security principles.
Trust model
ZTNA operates on a "never trust, always verify" principle, which means each access request must be authenticated, authorized, and continuously validated. VPNs, on the other hand, establish a secure tunnel to the organization's network, and once a user is connected, they are often granted broad access to resources.
Access control
Zero Trust Network Access enforces granular, context-aware access policies based on user identity, device, and other factors. Access is granted on a need-to-know basis and limited to specific applications or services. VPNs provide network-level access, which can potentially expose a larger attack surface to unauthorized users or malware.
Lateral Movement
ZTNA eliminates the possibility of lateral movement by granting access solely to necessary resources. In contrast, VPNs often provide users with access to the full internal network, which attackers could exploit.
User experience
ZTNA provides a more seamless user experience by granting access to specific applications without the need for a full network connection. VPNs often require users to establish a connection to the corporate network before accessing resources, which can be more cumbersome and slower.
Scalability and performance
ZTNA is typically more scalable and can handle a large number of users and connections more efficiently than traditional VPNs. This is particularly important in cloud-based or distributed environments, where traffic patterns and user locations can change rapidly.
Deliver Network and Security in the Cloud with ZTNA
Integrate Open Systems ZTNA with our cloud-based Managed SASE service for maximum protection and security. Begin your SASE journey with ZTNA and add our other services – Secure Web Gateway, Mobile Entry Point, Firewall, and CASB – as needed. You can conveniently manage all these services from a unified interface.
ZTNA is available as a stand alone product or as an add-on product to any of our Managed SASE service plans. Our plans combine 24×7 expertise focused on connecting and protecting users, apps, sites and clouds – all unified on an intelligent platform.

Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us


