
Higher Education
Simplify Network and Security Operations On and Off Campus
Higher education institutions’ primary focus is their faculty, staff, and student operations, which means keeping everything running smoothly between interconnected devices on and off campus. Sensitive data, including student information, needs to be protected within the infrastructure, and that’s no easy task for IT leaders. On top of that, there are budget constraints to balance against the potential risks of breaches and attacks.

IT Security that Exceeds Expectations
We bridge the gap in your institution by helping your IT team develop and maintain a security strategy that covers your entire environment. Our white-glove service gives IT leaders more time to dedicate and focus on student and faculty priorities. We deliver the broad network and security experience necessary to avoid the reputational damage that accompanies breaches and attacks.

Current IT Challenges in Higher Education
Heterogeneous Environment
Securely interconnect a zoo of gadgets and devices to maintain a consistent strategy and policies in a zero-trust environment.
Understaffed IT and Outdated Skillsets
Focus on supporting your end-users in day-to-day operations while offloading 24x7 security maintenance, monitoring, and trouble- shooting to a SOC.
Breaches and Cyberattacks
Develop a customized risk-based strategy to manage a large attack surface and protect sensitive data. Cover the whole kill chain and stay tuned to real alerts.
Cost Savings
Budget upfront for an all-inclusive SOC without hidden charges, providing flexibility to phase prod- ucts in or out in a multi- point life cycle.
Securely Manage a Heterogeneous Environment
In the dynamic environment of higher education, where users are constantly evolving, and changes are frequent, there is a need for clear security zones and policies. In addition to laboratory sensors and server infrastructure with legacy applications, there is a myriad of end-user devices to deal with as part of a standard BYOD strategy.
Open Systems configures and takes care of a flexible network architecture that makes frequent dynamic changes easy. Remote work is secure, easy to configure and manage, with our Mobile Entry Point (MEP) service.
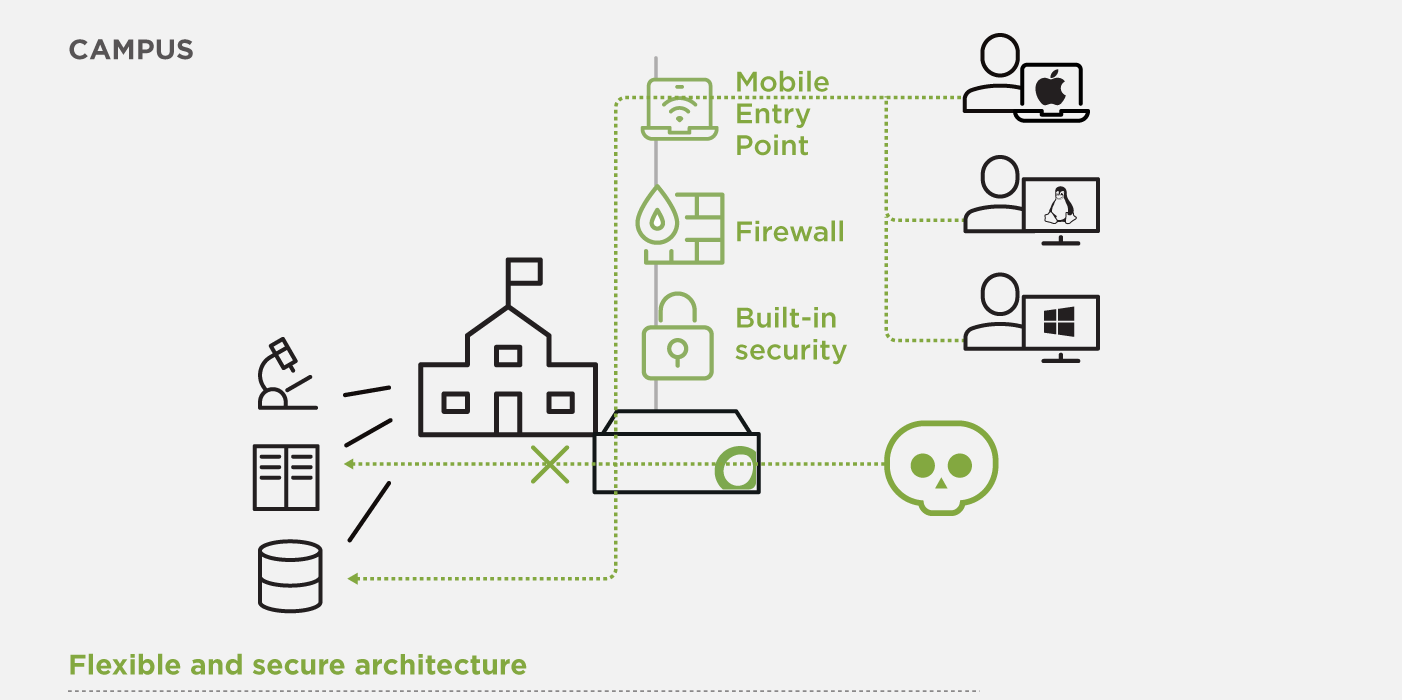
Balance Daily Operations with IT Staff and Skillsets
Legacy devices, such as laboratory machines, may not support web proxies – rendering them vulnerable. In an already complex network and security design, these assets should be taken care of, especially if a vulnerable device is compromised; the network must have controls to prevent the internal spread of infections.
Open Systems solutions address these challenges with a variety of integrated technologies which come with a premium service: 24×7 expert-level support and continuous technical consulting.
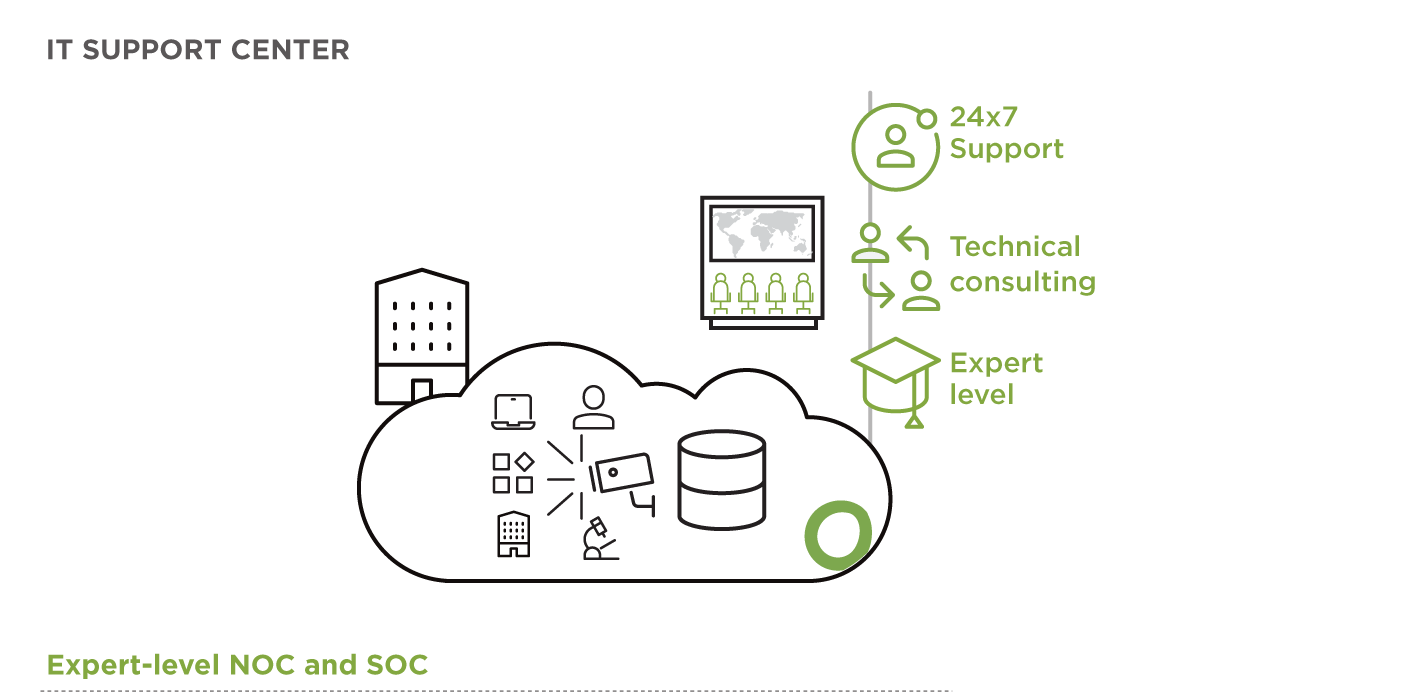
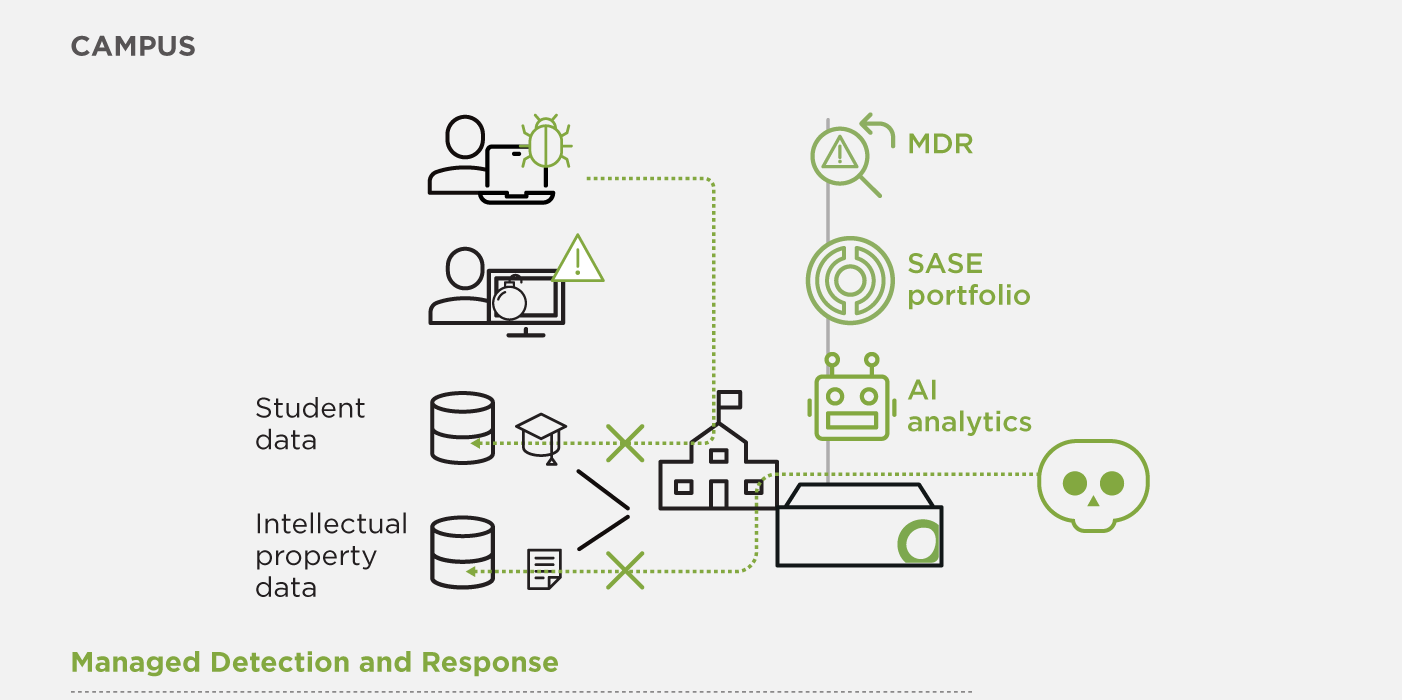
Cyberattack Prevention and Mitigation
It’s clear these days that cyberattacks are a matter of when, not if. Open Systems’ MDR platform provides a best practice framework for detecting threats, and it will continually evolve to keep pace with the changing nature of modern cyberattacks.
Whereas our Secure SD-WAN protects you against external threats with built-in, best-of-breed security features, MDR covers the whole kill chain. Our expert-level support (NOC) engineers respond to – and coordinate all actions – in the event of a security incident.
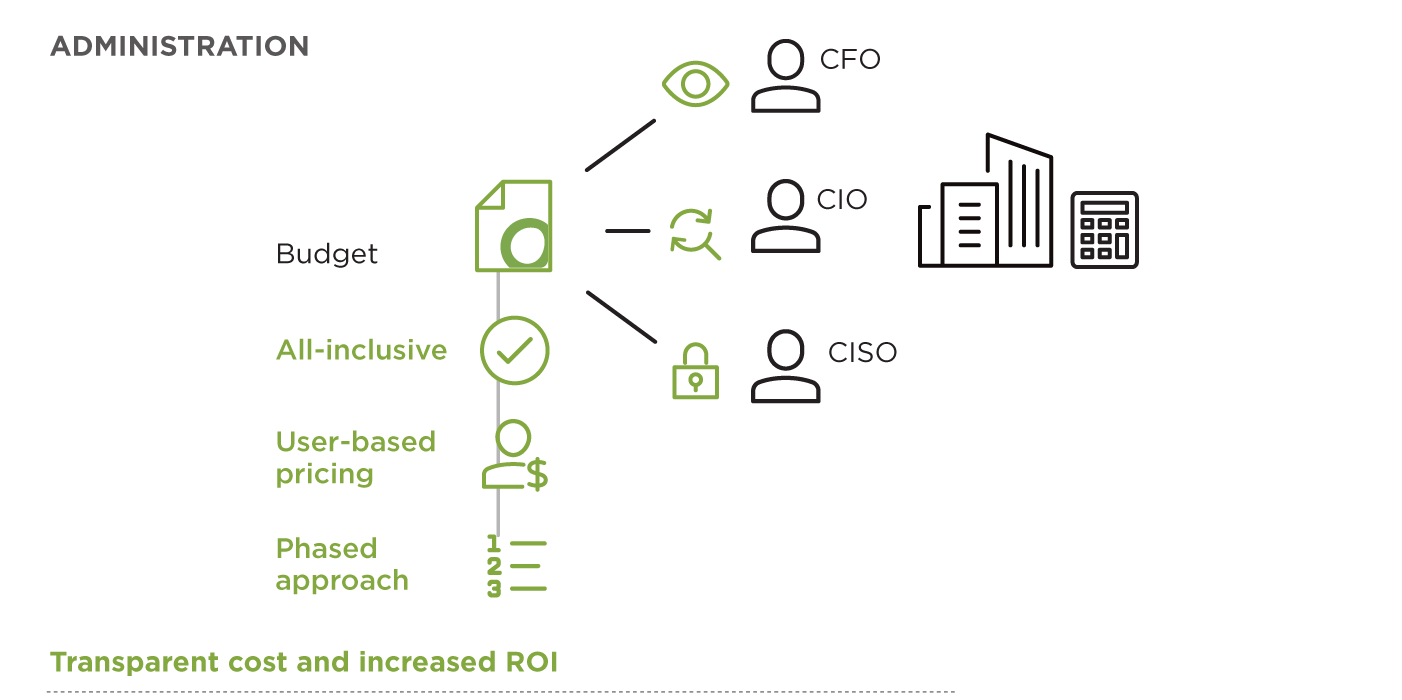
Save Costs, Keep Service Management Flexibility
The service pricing of Open Systems is flexible so that you can align the phase-out of your older products while you phase-in new services and architecture at a budget-friendly cost.
Benefit from transparent, user-based pricing without hidden costs. Leverage your existing Microsoft investments with Open Systems services, perfectly complementing or integrating with them.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us


