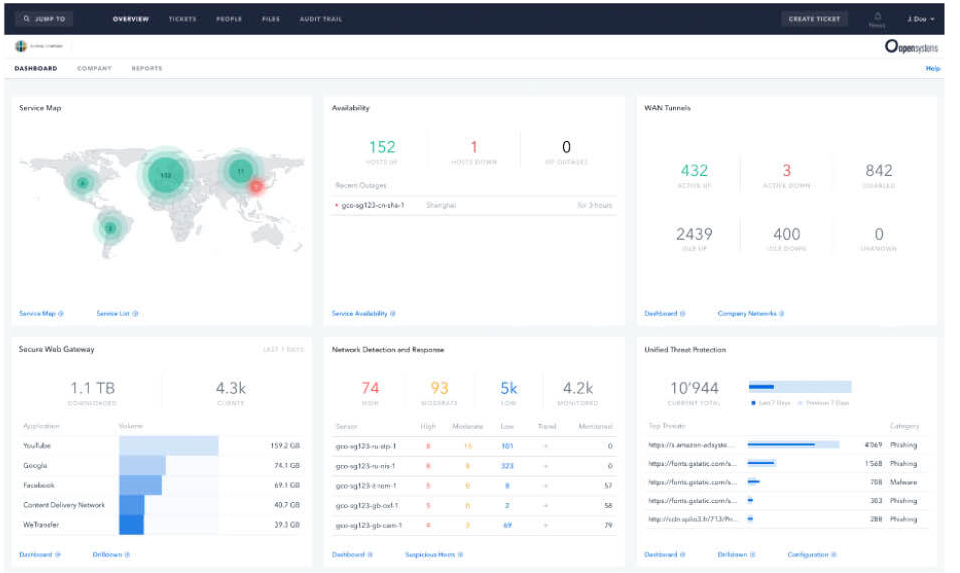
Threat Protection
We Prevent Your Network from Becoming a Competitive Disadvantage
In today’s environment, cyber attacks are increasingly sophisticated and global in scope, affecting nearly every business. Choose the Advanced Threat Protection add-on to complement our Secure SD-WAN packages and the Secure Email Gateway to gain an effective advantage in the marketplace.
Advanced Threat Protection Delivers
Personalized Phishing Protection
Leverage both our Secure Web and Email Gateways
Single Aggregator of Threat Intelligence
Provide a summary of feed info to multiple services
Selected Zero-Hour Feeds
Keep up with the speed of attackers and get the most recent IOCs from selected commercial providers.
Add Additional Feeds for Extra Security
More feeds increase the probability of blocking threats
There are many threat intelligence feeds available in the marketplace today, but you have to know which are useful and in what way. Open Systems curates a select group of high quality feeds, delivering rich real-time intelligence to all Secure SD-WAN security features and enabling consistent protection across the network. Avoid double-spending on external feeds, and add additional feeds to achieve even higher levels of protection.
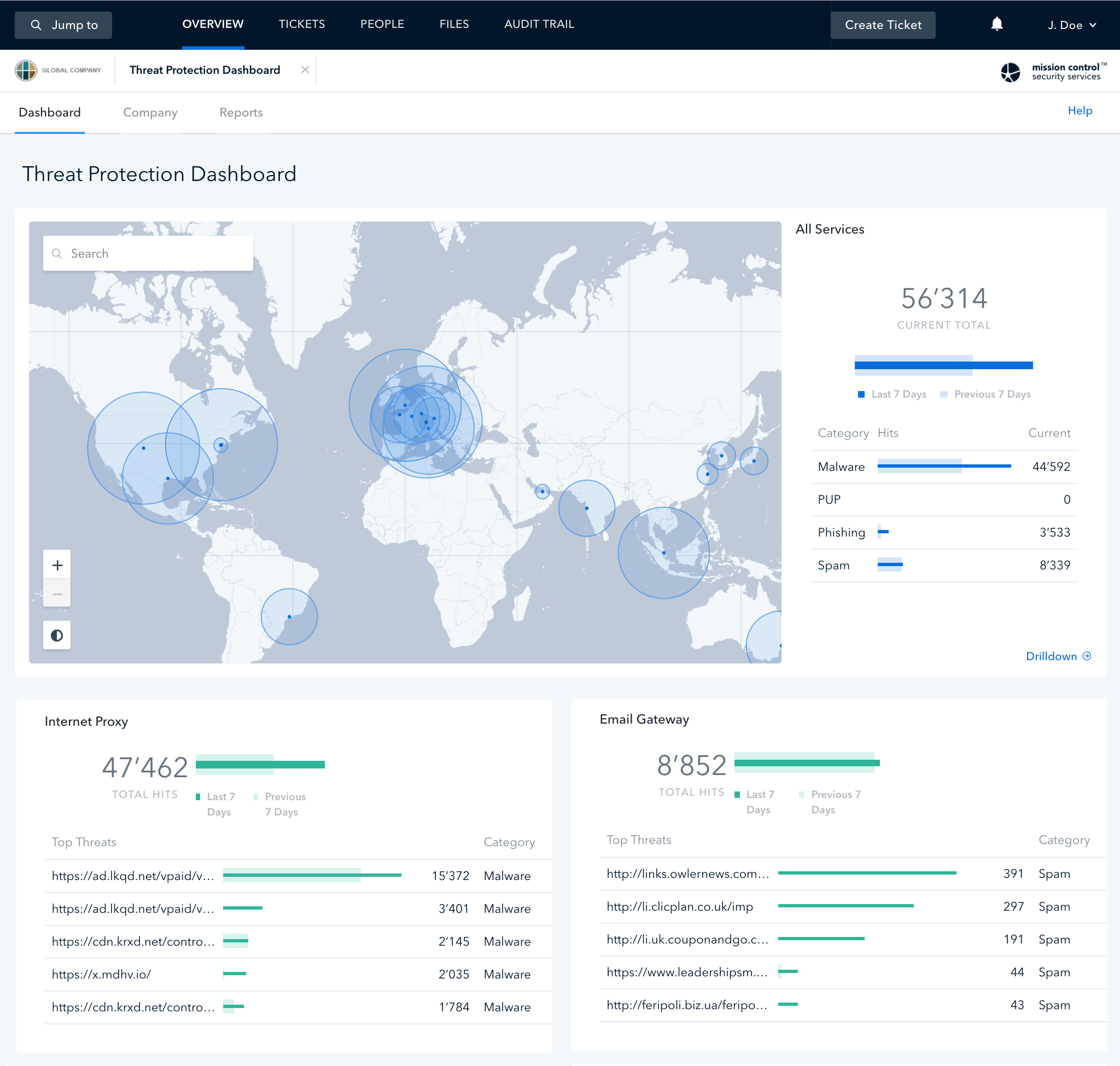
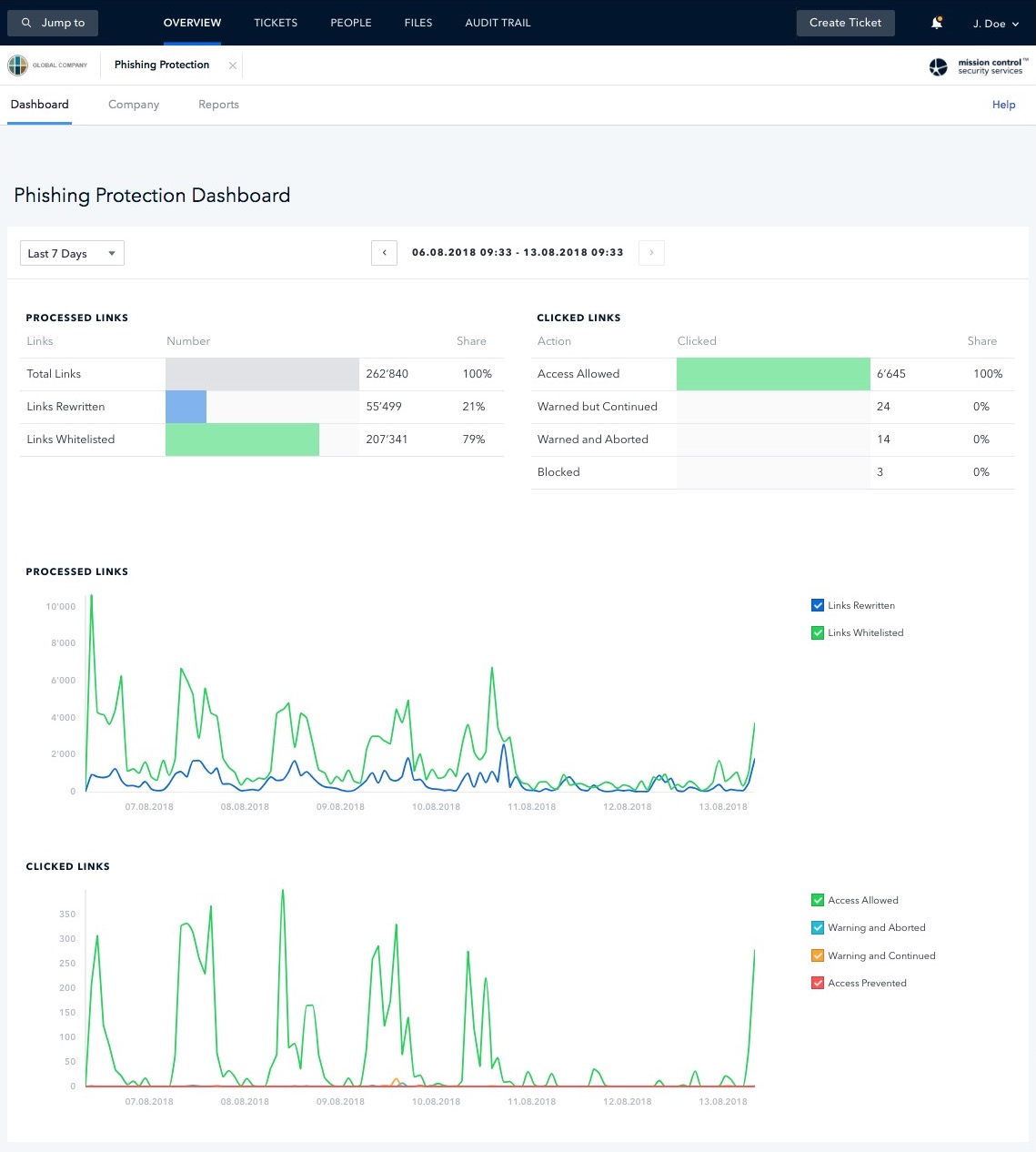
Phishing attacks are all too common today, and carry significant risk for the enterprise. Our Secure Email Gateway and Secure Web Gateway provide a robust defense against this type of malicious actor through comprehensive scanning and filtering of traffic, DMARC enforcement, and global access policies. The advantage of having both is they are able to tag and verify all suspicious URLs contained within email traffic, and alert users when necessary.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us