
Secure Web Gateway
Cloud-based SWG controls and protects your users’ web traffic anywhere, anytime.
The Open Systems Secure Web Gateway is a comprehensive web security solution that combines advanced threat protection, secure access controls, and intelligent web filtering to provide organizations with a secure and productive web browsing experience.
Protect Yourself from Web Threats
Our cloud SWG helps protect you from web threats and enforces your business policy.
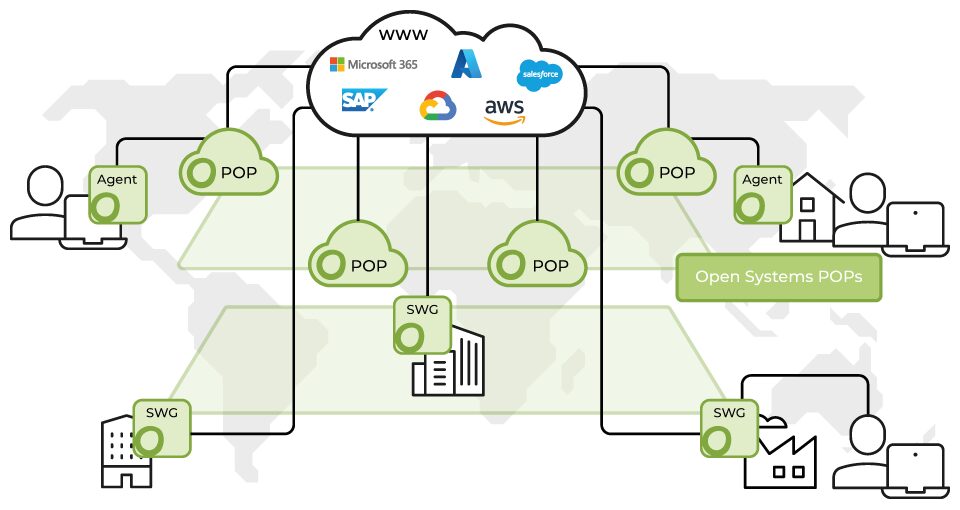
Global Presence
Leverage Open Systems’ global distribution of PoPs to provide fast and secure access anywhere in the world.
The cloud-based architecture extends to on-premises and IaaS deployments guaranteeing scalability and performance for your growing organization.
Advanced Threat Protection
Sophisticated threat protection mechanisms shield users against various web-based threats such as malware, phishing attacks, ransomware, on the Secure Web Gateway (SWG) as well as on the Firewall and Secure Email Gateway.
Web Traffic Control
Granular web filtering capabilities, allow administrators to define policies and control access to the Internet.
Ensure compliance and reduce exposure to inappropriate or non-business-related content thanks to easy-to-use policy controls.
Secure Access and Authentication
Single sign-on (SSO), multi-factor authentication (MFA), and integration with identity and access management (IAM) solutions ensure that only authorized users with valid credentials can access the web.
Leverage Open Systems’ global distribution of PoPs to provide fast and secure access anywhere in the world.
The cloud-based architecture extends to on-premises and IaaS deployments guaranteeing scalability and performance for your growing organization.
Sophisticated threat protection mechanisms shield users against various web-based threats such as malware, phishing attacks, ransomware, on the Secure Web Gateway (SWG) as well as on the Firewall and Secure Email Gateway.
Granular web filtering capabilities, allow administrators to define policies and control access to the Internet.
Ensure compliance and reduce exposure to inappropriate or non-business-related content thanks to easy-to-use policy controls.
Single sign-on (SSO), multi-factor authentication (MFA), and integration with identity and access management (IAM) solutions ensure that only authorized users with valid credentials can access the web.
How Does SWG Work?
Authentication
Authentication of users enables the creation of different policy groups and different levels of malware protection, URL filtering, and SSL scanning.
URL Filter
URL Filter enforces an organization’s internet access policy and protects against risks associated with employees’ internet use.
TLS interception and Certificate Validation
TLS interception and certificate validation applies malware protection and enforces browsing policy on encrypted traffic. Certificates are also verified
to only allow access to websites with valid certificates.
Malware Protection
Malware protection uses machine learning, heuristics and generics to identify malicious code with near zero false positive.
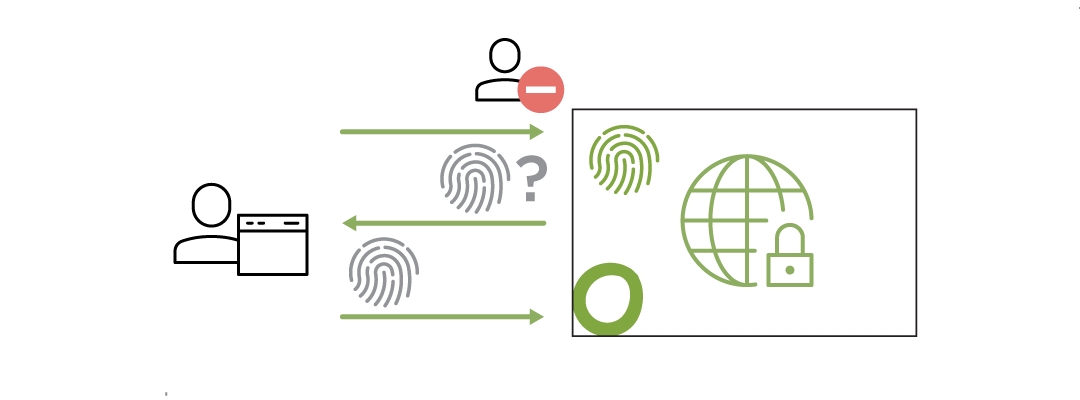
Authentication of users enables the creation of different policy groups and different levels of malware protection, URL filtering, and SSL scanning.
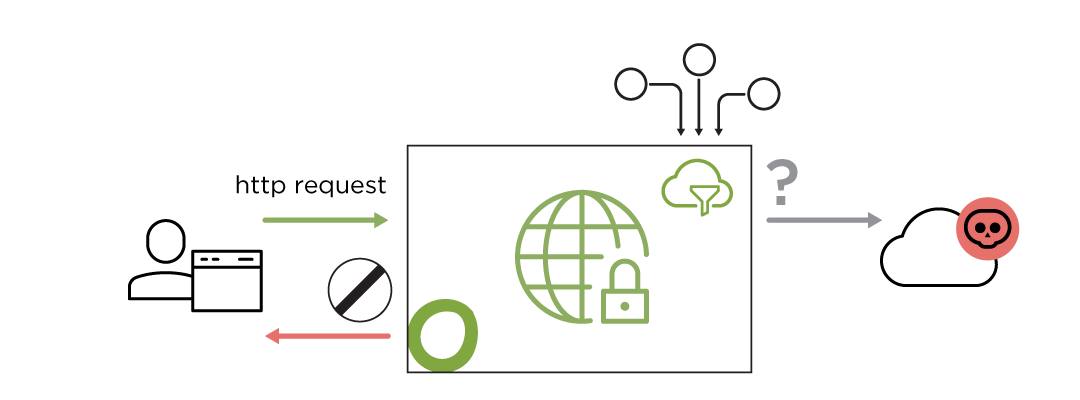
URL Filter enforces an organization’s internet access policy and protects against risks associated with employees’ internet use.
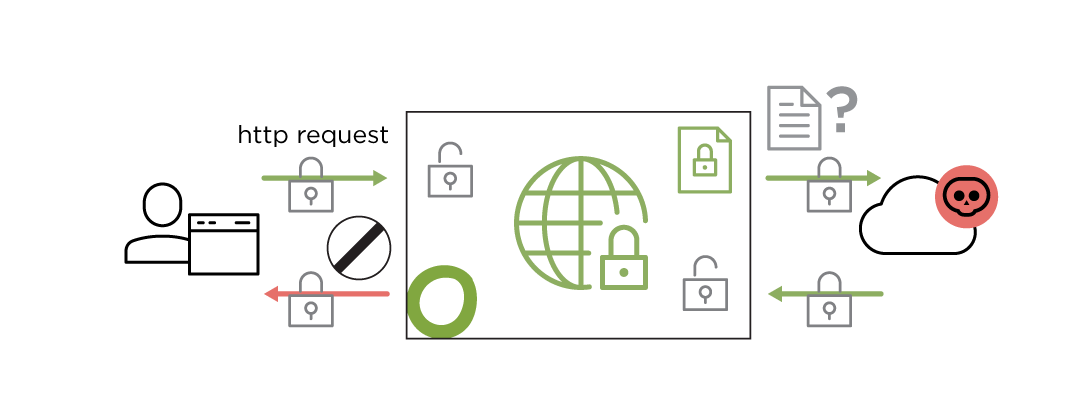
TLS interception and certificate validation applies malware protection and enforces browsing policy on encrypted traffic. Certificates are also verified
to only allow access to websites with valid certificates.

Malware protection uses machine learning, heuristics and generics to identify malicious code with near zero false positive.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us



