
Firewall
Simplify and Enhance Network Security
To protect your WAN from external threats such as web threats, cyberattacks, or unauthorized access, a state-of-the-art firewall is still essential in perimeter security. Threats not only come from the outside but increasingly from inside your WAN.
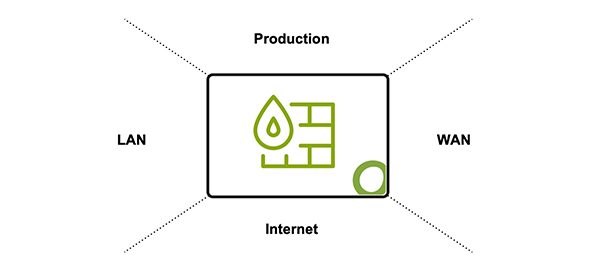
Our next-gen firewall protects your organization‘s network servers and end-user machines not just by filtering traffic, but by leveraging multiple security zones within the network itself.
Deliver Powerful Protection
Advanced Filtering of Network Traffic
Multi-Zone Approach to Security
Global and Local Policy Flexibility
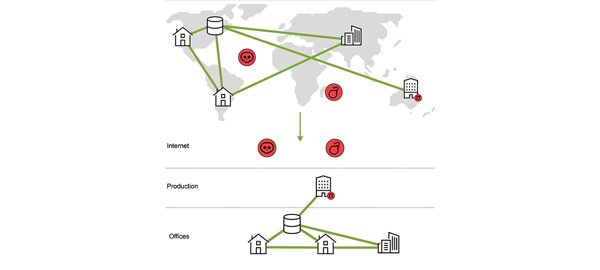
How We Protect Your Network
Our multi-zone network firewall policies strike the right balance between security and operability.
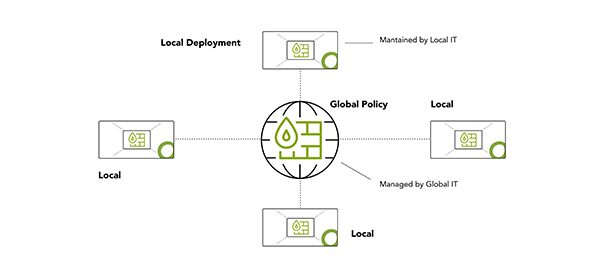
- Global IT defines a global corporate security policy by defining general zone transitions
- Local IT maintains and updates local firewall objects. In addition, exceptions or new zones can be defined in collaboration with global IT.
Policy
Through smart layer 7 packet inspection, applications can be detected automatically on the network and used for filtering by the firewall. This helps to simplify the firewall policy – instead of implementing several firewall rules to allow SaaS application traffic with different protocols, ports, and destination IPs, logic can be summarized to one application rule.
Security
Assets from different security zones can only communicate via certain applications or protocols, as defined by individual firewall rules, and security zones can be shielded from each other by restricting or blocking their zone transitions. For more granular filtering, individual site-specific firewall rules can be implemented to allow access on certain protocols for assets from different zones.
Operability
Through the zoning concept, a lot of different network segments or interfaces can be summarized to one zone of a certain security level. Consequently, one simple zone transition policy can be defined instead of implementing several different access rules for each one-to-one communication.
Management
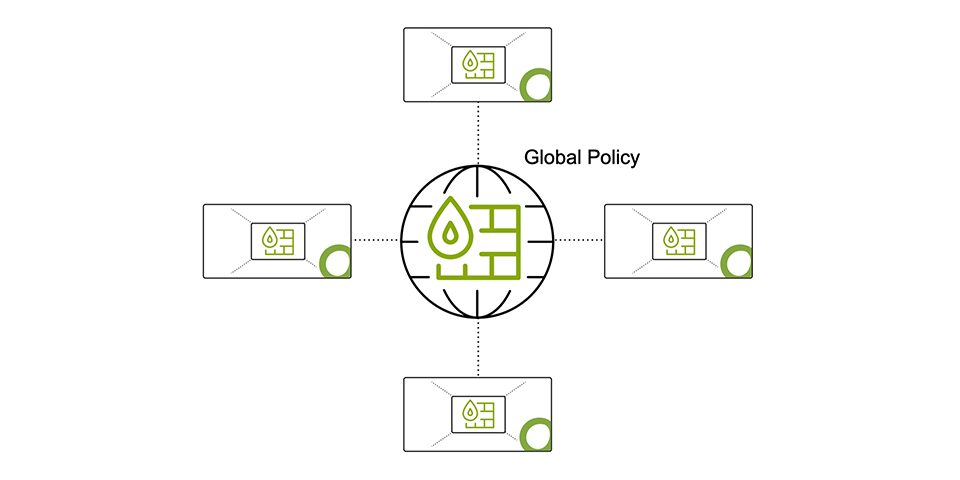
From a policy management perspective, we offer a hybrid administration model that allows an organization’s global IT to enforce a security policy while providing flexibility for local IT to customize the policy where needed.
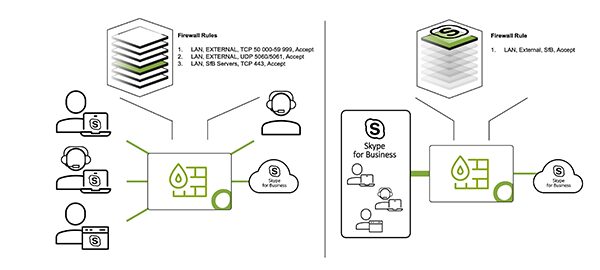
Through smart layer 7 packet inspection, applications can be detected automatically on the network and used for filtering by the firewall. This helps to simplify the firewall policy – instead of implementing several firewall rules to allow SaaS application traffic with different protocols, ports, and destination IPs, logic can be summarized to one application rule.

Assets from different security zones can only communicate via certain applications or protocols, as defined by individual firewall rules, and security zones can be shielded from each other by restricting or blocking their zone transitions. For more granular filtering, individual site-specific firewall rules can be implemented to allow access on certain protocols for assets from different zones.
Through the zoning concept, a lot of different network segments or interfaces can be summarized to one zone of a certain security level. Consequently, one simple zone transition policy can be defined instead of implementing several different access rules for each one-to-one communication.
From a policy management perspective, we offer a hybrid administration model that allows an organization’s global IT to enforce a security policy while providing flexibility for local IT to customize the policy where needed.
- Global IT defines a global corporate security policy by defining general zone transitions
- Local IT maintains and updates local firewall objects. In addition, exceptions or new zones can be defined in collaboration with global IT.
A Multi-Zone Approach Ensures Security and Trust
Open Systems’ firewall architecture introduces distinct security zones. These zones segment the global network into different zones of security and trust and enable communication between zones to be properly controlled.
With this feature, we can filter traffic at transitions between different security zones and maintain security within each zone. Thus, the overall integrity of the SD-WAN can be shielded not only from internet threats but also from doubtful internal sources in untrusted security zones.
How To Buy
Firewall is available in our Enterprise and Enterprise+ SASE service plans. Our plans combine 24×7 expertise focused on connecting and protecting users, apps, sites and clouds – all unified on an intelligent platform.

Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us



