Gartner Calls SASE Transformational

The networking, SD-WAN, and cloud access security markets have recently been abuzz with a new cloud-delivered technology framework that promises to alleviate several of IT’s most severe pain points. Industry research firm Gartner has named the framework Secure Access Service Edge (SASE), pronounced “sassy”, and called it “transformational”. The emergence of SASE reflects the digital transformation happening in today’s enterprises, which heightens the requirements digital businesses have for dynamic access.
What exactly is SASE?
In its recently published report, The Future Network Security Is in the Cloud, Gartner defined SASE as “an emerging offering combining comprehensive WAN capabilities with comprehensive network security functions (such as SWG, CASB, FWaaS, and ZTNA) to support the dynamic secure access needs of digital enterprises.”
What’s driving SASE adoption?
Let’s take a quick look at why SASE is not a fad, but the future of networking and secure cloud access. Today, more users, devices, applications, services, and data reside outside of the enterprise than inside. Increasingly, remote and mobile workforces rely on myriad devices—all needing access to data and applications and many looking to connect to enterprise networks from anywhere. This trend also puts sensitive data and core business applications outside the firewall on everything from public clouds to mobile devices that can be easily lost or stolen.
Traditional hub-and-spoke network and security architectures weren’t designed for these types of more dynamic, fluid, and distributed usage patterns. Let’s look at two representative challenges in particular.
First, remote users often encounter performance issues, which are typically caused by network and service chain latencies. This is because, in conventional network architecture, traffic needs be tromboned through a gauntlet of network security devices in the data center miles away.
Second is the effects of security controls—or lack thereof. If developers have to wait days for IT to update firewall policies every time they bring up new apps into the cloud, productivity is going to take a hit. If users can download and upload data to any SaaS or cloud app, data leakage is surely taking place. The point is that performance/usability and security issues vie for IT’s attention, often with demands that are at odds.
Consequently, IT finds itself overwhelmed. Teams struggle to keep up with the increasing expectations and requirements from all sides (users, business, and security) because they are hamstrung by structural issues. For one, ripping out the existing hub-and-spoke network to improve user experience is not viable. They also lack the tools and capabilities (not to mention the staff) to make sound security decisions.
This leaves teams under constant pressure to perform a delicate balancing act between blocking flows that could hinder business agility and allowing flows that could harm the business. Furthermore, IT teams typically have little actionable visibility into what’s happening in their environments and are often forced to make potentially consequential decisions based on incomplete information. As a result, they often end up putting in security policies that are either too strict or too loose. And, let’s not forget the constant challenge of keeping those policies up to date or in sync across devices.
In the end, no one is happy. Consequently, many users simply bypass their corporate network altogether if they can. The result can comprise a litany of undesirable outcomes and security risks, including shadow IT, data leakage, malware, and data exfiltration.
How does SASE help?
Fundamentally, SASE turns traditional networking models upside down by putting access to networking and security functions as close to the user as a cloud-based service. Furthermore, the highly integrated architecture means users get the best possible performance while IT—through the SASE provider—can enforce more precise, up-to-date security policies.
According to Gartner: “SASE capabilities are delivered as a service-based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions.”
More specifically, the SASE architecture promotes:
- Tight integration of “comprehensive WAN” and “network security functions” to reduce the complexity and latency associated with loosely coupled point products
- Ubiquitous, well-peered cloud services (complemented by “thin branch” devices) that greatly reduces end-to-end network latency
- Real-time, context-based policy capabilities that help improve policy accuracy and efficacy
- Delivery of SASE as a service that reduces operational overhead
Tight integration of networking and security functions
A fundamental requirement of a SASE offering is tight integration of networking and security functions. Here, the core SASE technologies include SD-WAN, WAN optimization, firewall, secure web gateway (SWG), cloud access security broker (CASB), data leakage protection (DLP), and Zero Trust Network Access/Security Defined Perimeter (ZTNA/SDP).
Gartner specifically recommends that enterprises “avoid SASE offerings that are stitched together. Closely evaluate the integration of the services and its ability to be orchestrated as a single experience from a single console and a single method for setting policy.” In practice, this requires architectural capabilities that enable different services to work together and share common data sets and policies.
Maximum integration, optimal cloud service, minimal latency
The next requirement is to offer integrated functions with the least network latency. That requires a SASE solution with:
- Broadly (globally) distributed footprint of POPs (points of presence) to ensure that user traffic from anywhere can get to SASE services with minimal latency
- Dense, low latency peerings with other internet and cloud providers so that user traffic can be forwarded to its final destination as directly as possible
Such an optimized cloud network can (and should) be complemented by on-prem (physical or virtual) services to serve larger offices.
It goes without saying that cloud-based SASE services should operate in ways we expect of cloud services – such as automated deployment, elastic scaling, continuous integration / continuous deployment, continuous monitoring, automated recovery, etc. In short, a SASE service should be cloud-native so that it can seamlessly meet changing conditions.
Policies need context
Unlike traditional, rigid network-based policies, with SASE services IT needs capabilities to enforce policies based on user- and service-centric contexts such as application ID and user ID (as well as other contexts like risk, device profile, time of day, location, or sensitivity of data accessed). Again, according to Gartner, IT also needs “the ability to continuously assess risk/trust throughout the sessions.”
Context-based policies allow for more tailored, accurate policies that are easier to understand, monitor, and maintain. Keeping policies in sync and up to date (across multiple SASE services) is a far easier task with identity/context-centric policies. And this, in turn, leads to lower operational overhead, fewer errors, and greater security.
SASE by definition functions as a service
SASE by definition is a service. IT should not have to deploy and manage multiple disparate products as they do today. Still, you should consider the degree of involvement your IT staff will have in managing the SASE service. Do you want a fully managed service in which the SASE provider handles everything (service delivery, management, monitoring, troubleshooting)? Or do you want to retain certain “self-service” capabilities like making firewall rule changes, updating web proxy whitelists?
Whether fully managed or self-service, you should be sure to look into the SLAs of such offerings. What is the turnaround time when problems arise as they inevitably will? Does the provider help develop and maintain security policies? And so on. Do interview current and former users of the provider.
Open Systems SASE services
Open Systems has been offering several highly integrated SD-WAN and security functions as a service for both cloud and on-prem environments even before SASE became the next big thing. In fact, we began offering SD-WAN services some five years ago.
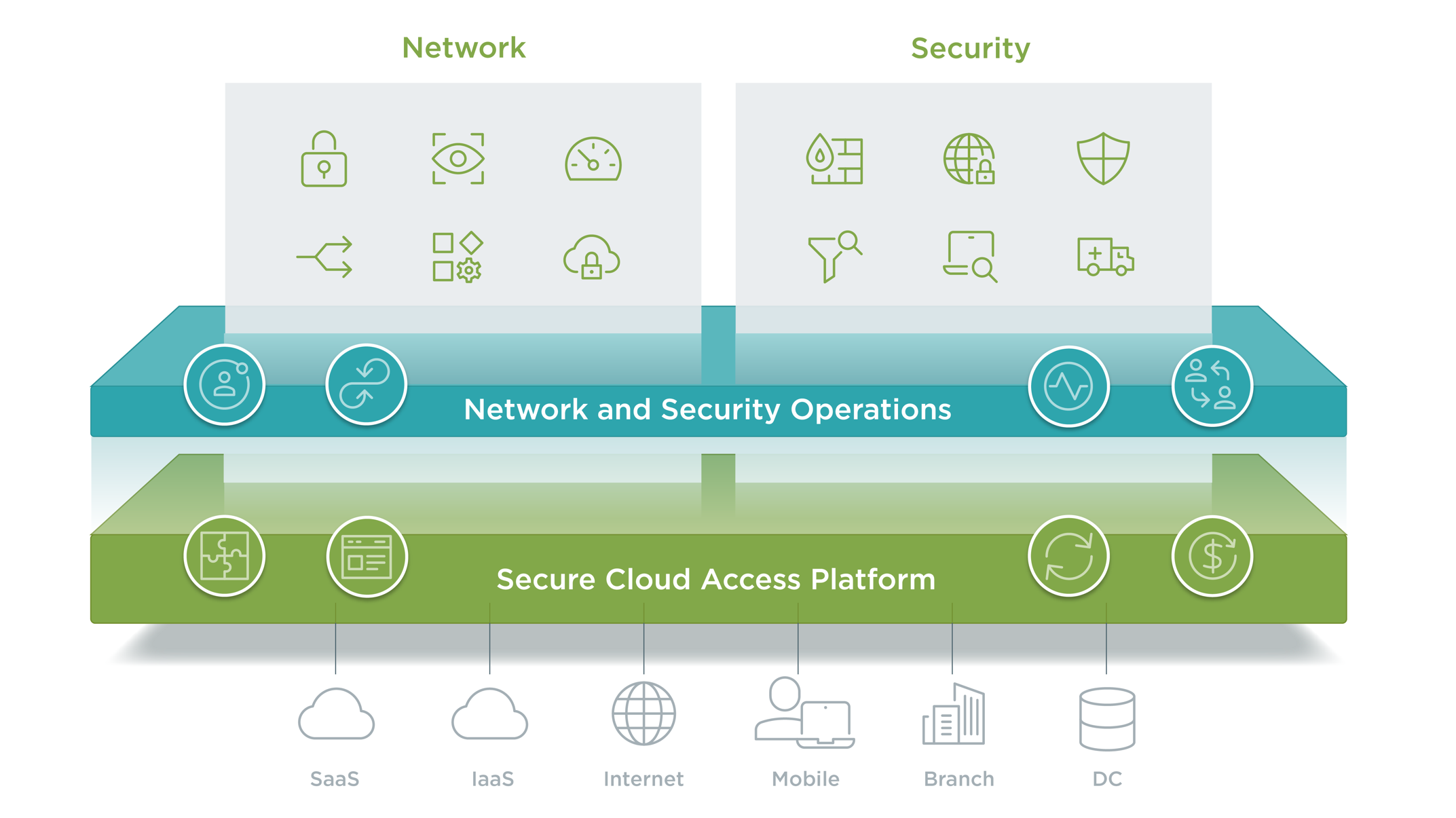
Here are some of the highlights of the Open Systems SASE solutions available today:
- Integrated network and security services, including SD-WAN, App Optimization, FW, SWG, CASB, and VPN. (these include services such as Secure Email Gateway (SEG) and Endpoint Detection and Response (EDR) that are not part of the SASE services as defined by Gartner today)
- Integrated services that can be delivered in on-premises environments as well as in the major public clouds such as Azure and AWS
- Application and identity-aware, and integrates with cloud identity providers
- Open Systems Mission Control provides a truly world-class NOC and SOC service
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us

 Open Systems
Open Systems