
Standard Email Security Service
Secure the Essentials
Email remains the #1 attack vector in a rapidly evolving digital threat landscape. Phishing, spoofing, and compliance risks plague organizations daily, especially in remote work setups. Open Systems’ Standard Email Security provides robust protection against spam, malware, phishing, with built-in SPF, DKIM, DMARC, and encryption to ensure message authenticity and security – offering a reliable defense without complexity. By combining best-practice configurations with expert-led operations, we help businesses regain control over their communications and protect sensitive data – securely and compliantly.

Benefits
Proven Email Protection
Industry-standard security features against spam, malware, phishing, with built-in SPF, DKIM, and DMARC to block spoofed messages and protect your brand’s reputation.
Encryption by Design
TLS-based encryption as a service ensures secure communication across partners and clients without disrupting email delivery.
Effortless Configuration Support
Experts handle setup and policy adjustments for sender validation and routing, ensuring secure delivery from day one.
Included in the Service
Customer Portal
Real-Time Visibility
Use Case: Security teams need to monitor inbound threats and diagnose delivery issues.
Benefit: Our customer portal provides real-time and historical data with drill-down insights.
Open Systems Difference: Role-based access and audit-ready logs offer deep insights with high security.
Expert-level Support
Expert-Guided Configuration
Use Case: Teams need support configuring encryption or sender verification for new tools.
Benefit: Our 24×7 support team ensures rapid, correct SPF/DKIM setups and secure TLS communication.
Open Systems Difference: Specialists guide implementation with scale and precision.
Designated Account Management
Custom Policy Management
Use Case: Executives want email forwarding or brand protection via DMARC.
Benefit: Technical Account Managers handle complex rules and support with DMARC.
Open Systems Difference: Hands-on, ongoing support ensures tailored, business-aligned security.
Real-Time Visibility
Use Case: Security teams need to monitor inbound threats and diagnose delivery issues.
Benefit: Our customer portal provides real-time and historical data with drill-down insights.
Open Systems Difference: Role-based access and audit-ready logs offer deep insights with high security.
Expert-Guided Configuration
Use Case: Teams need support configuring encryption or sender verification for new tools.
Benefit: Our 24×7 support team ensures rapid, correct SPF/DKIM setups and secure TLS communication.
Open Systems Difference: Specialists guide implementation with scale and precision.
Custom Policy Management
Use Case: Executives want email forwarding or brand protection via DMARC.
Benefit: Technical Account Managers handle complex rules and support with DMARC.
Open Systems Difference: Hands-on, ongoing support ensures tailored, business-aligned security.
Service Components
Sender Verification
Verifies senders using SPF, DKIM, and DMARC to prevent spoofing. Exclusion/block lists and policy controls enable granular access management.
Content Analysis
Uses heuristic and signature-based filters plus threat intel to detect malware, spam, and phishing attempts – including malicious URLs.
Policy Enforcement
Automated policies route, tag, or encrypt emails based on content, sender, or risk profile – supporting compliance and secure communication.
How it works
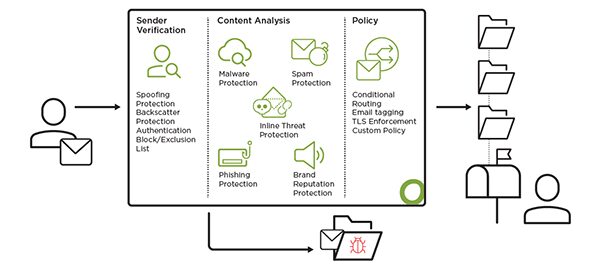
Sender Verification
Standard Email Security starts with strong sender authentication. It enforces SPF, DKIM, and DMARC to validate the origin of inbound emails and prevent spoofing or abuse of your domain. TLS encryption is applied to secure communication channels, ensuring messages are transmitted safely between mail servers. You can define allow/block lists and configure connection policies either at the SMTP layer or through policy-based rules – giving you flexible control over who can send to your users.
Content Analysis
Once emails are accepted, they pass through a multi-layered content inspection engine. This includes signature-based malware detection, heuristic spam filtering, and real-time threat intelligence. The system scans not just attachments but also embedded links and content for signs of phishing, malware, or policy violations. URLs are evaluated in real time, and suspicious messages are tagged or quarantined with clear warnings to users, improving their security awareness.
Policy Enforcement
Every message is evaluated against customizable policy rules. Based on content, sender, or threat level, emails can be routed to quarantine, tagged for archiving, or automatically encrypted. Organizations can set up dynamic policies for departments or individuals – for instance, requiring encrypted delivery for finance-related communications. Policy flexibility allows administrators to enforce compliance and protect sensitive data with minimal manual intervention.
Standard Email Security starts with strong sender authentication. It enforces SPF, DKIM, and DMARC to validate the origin of inbound emails and prevent spoofing or abuse of your domain. TLS encryption is applied to secure communication channels, ensuring messages are transmitted safely between mail servers. You can define allow/block lists and configure connection policies either at the SMTP layer or through policy-based rules – giving you flexible control over who can send to your users.
Once emails are accepted, they pass through a multi-layered content inspection engine. This includes signature-based malware detection, heuristic spam filtering, and real-time threat intelligence. The system scans not just attachments but also embedded links and content for signs of phishing, malware, or policy violations. URLs are evaluated in real time, and suspicious messages are tagged or quarantined with clear warnings to users, improving their security awareness.
Every message is evaluated against customizable policy rules. Based on content, sender, or threat level, emails can be routed to quarantine, tagged for archiving, or automatically encrypted. Organizations can set up dynamic policies for departments or individuals – for instance, requiring encrypted delivery for finance-related communications. Policy flexibility allows administrators to enforce compliance and protect sensitive data with minimal manual intervention.
What Sets Our Solution Apart
Reliable Core Protection
Strong baseline defense with trusted standards – SPF, DKIM, DMARC, and TLS – protects domains and users from impersonation.
Seamless Administration
Policy tuning and sender config handled via portal or experts – reducing operational effort and error.
Compliant by Default
Built-in encryption and logging support DORA, NIS2, GDPR, and other compliance mandates without extra tools.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us




