The Evolution of Quishing: How QR Code Phishing Bypasses Modern Security

Understanding the Quishing Threat
Quishing, or QR code phishing, represents a rapidly evolving threat in the cybersecurity landscape. These attacks leverage malicious QR codes embedded with harmful links to redirect unsuspecting victims to fake websites designed for credential theft. While Microsoft Defender for Office 365 and many Secure Email Gateways (SEGs) offer some protection against these attacks, their defenses are often incomplete or unreliable, particularly against sophisticated evasion techniques that we’ll explore in this post.
What makes quishing particularly effective is its ability to bypass both human inspection and traditional security filters. Unlike text-based phishing emails that users have learned to scrutinize, QR codes appear as innocuous black-and-white patterns that reveal nothing about their destination until scanned. Some existing security solutions can detect basic image-based QR codes, but struggle with advanced obfuscation methods. Compounding this vulnerability, while the malicious code arrives via corporate email with enterprise security, users typically scan these codes with personal mobile devices that lack corporate security controls, effectively bypassing the entire security stack.
The evolution of these attacks has been remarkable, progressing from standard MFA authentication requests to conditional routing and custom targeting, and now to sophisticated manipulation techniques specifically designed to evade the partial protections offered by mainstream security platforms.

Normal, image base, QR code with potentially malicious URL.
Advanced Evasion Techniques: Staying One Step Ahead
As security vendors have implemented QR code protection measures, attackers have responded with increasingly sophisticated evasion techniques. Here are the three primary methods being employed in the wild:
ASCII Art QR Codes: The Text-Based Trojan Horse
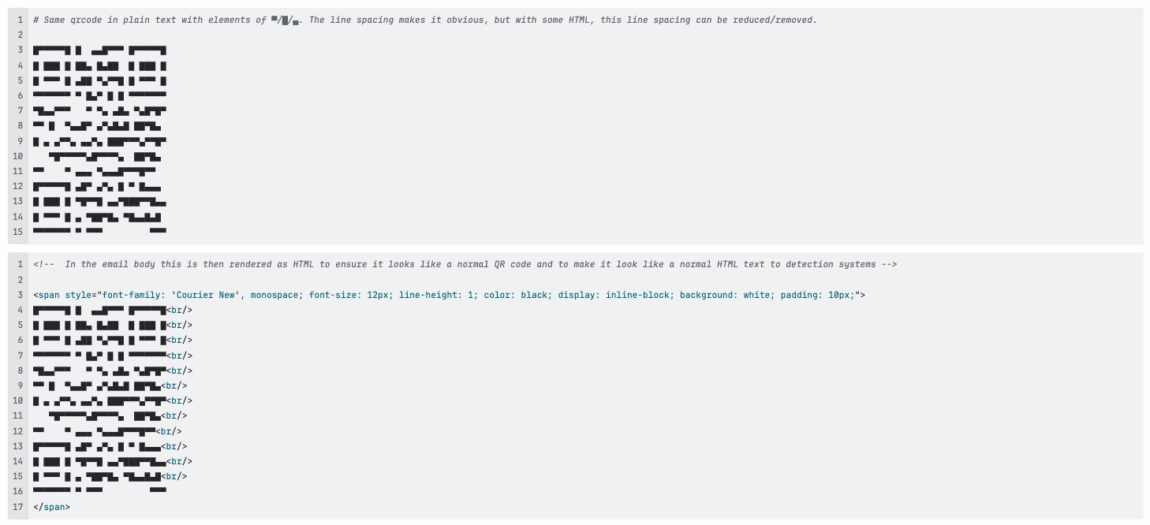
One of the most ingenious evasion techniques involves creating QR codes using HTML and ASCII characters rather than traditional images. Instead of embedding a standard image file, attackers construct QR codes entirely from text characters, creating what appears to be a normal QR code to the human eye but looks like harmless text to security scanners.
This ASCII-based approach specifically aims to bypass Optical Character Recognition (OCR) engines, the very technology that many security solutions rely on to detect and analyze QR codes. Since these ASCII-based QR codes aren’t technically images, traditional image-based security scans fail to recognize them as QR codes at all, allowing them to slip through undetected.

ASCII/UTF8 characters based QR code as seen by user.
In the email body this is then rendered as HTML to ensure it looks like a normal QR code and to make it look like a normal HTML text to detection systems
Split QR Codes: Divide and Conquer
Another technique involves splitting the QR code into two or more separate images within a phishing email. This approach exploits a fundamental weakness in how security scanners analyze email content.
When a QR code is divided into multiple parts, each individual piece appears benign to security scanners that analyze attachments and embedded images in isolation. Only when these pieces are visually combined, either through clever HTML positioning or when viewed by the recipient, does the complete, malicious QR code become functional. This technique effectively blinds automated security systems while maintaining full functionality for the end user.
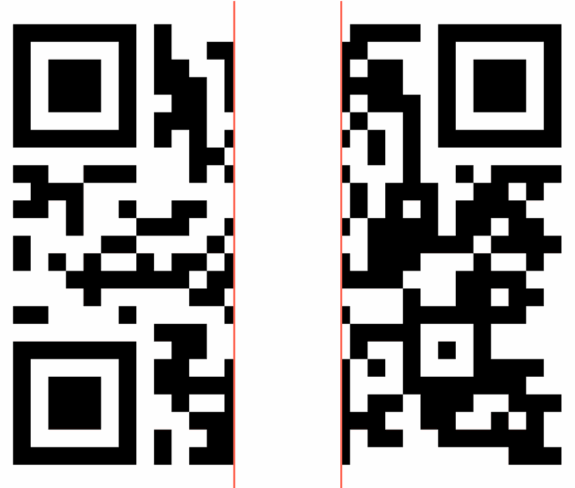
QR code split into two files that on their own are not recognized as a QR code.
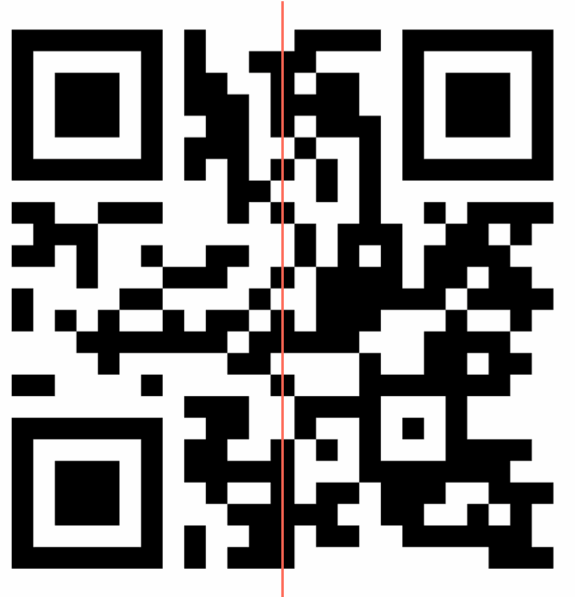
Moving these two files next to each other results in a valid QR code.

QR code as seen by user in the email.
Nested QR Codes: Creating Ambiguity
The nested QR code technique takes a different approach by embedding a malicious QR code within or around a legitimate one. This creates a visual ambiguity that confuses both security scanners and users.
The genius of this approach lies in its exploitation of how QR code readers prioritize information. Depending on the scanning angle, lighting conditions, or the specific reader being used, different codes might be interpreted. This creates ambiguity for scanners attempting to determine which code represents the actual threat, often leading to false negatives in detection systems.

One QR code embedded into another, making it random which one is picked up by the users phone or the detection software.
Defending Against Evolving Quishing Threats
As these sophisticated evasion techniques continue to evolve, security professionals must implement comprehensive defenses that address both the technical and human elements of these attacks. The key lies in multilayered protection that combines user awareness with advanced AI-driven detection capabilities capable of analyzing QR codes regardless of their format or obfuscation technique.
Essential defensive measures include:
- Educate users about QR code risks while ensuring compromised credentials cannot provide system access
- Deploy security solutions that automatically decode QR codes embedded in emails and analyze destination URLs for malicious indicators
- Leverage AI that visually locates QR codes within emails and uses machine learning to analyze QR code structures and context
Comprehensive Protection with Open Systems
Advanced Email Security from Open Systems protects users from quishing attacks through advanced extraction methods and contextual AI detection. The solution renders emails exactly as users would see them in their email client and captures this visual representation for analysis, effectively detecting ASCII and split QR codes that traditional scanners miss. By combining this visual analysis with comprehensive threat intelligence and contextual machine learning models, the solution identifies and neutralizes quishing attempts before they reach end users, ensuring that even the most sophisticated evasion techniques are detected and blocked.
Leave Complexity
Behind
To learn how Open Systems SASE Experience can benefit your organization, talk to a specialist today.
Contact Us

 Fabian Zeindler, Senior Product Owner E-mail Security
Fabian Zeindler, Senior Product Owner E-mail Security