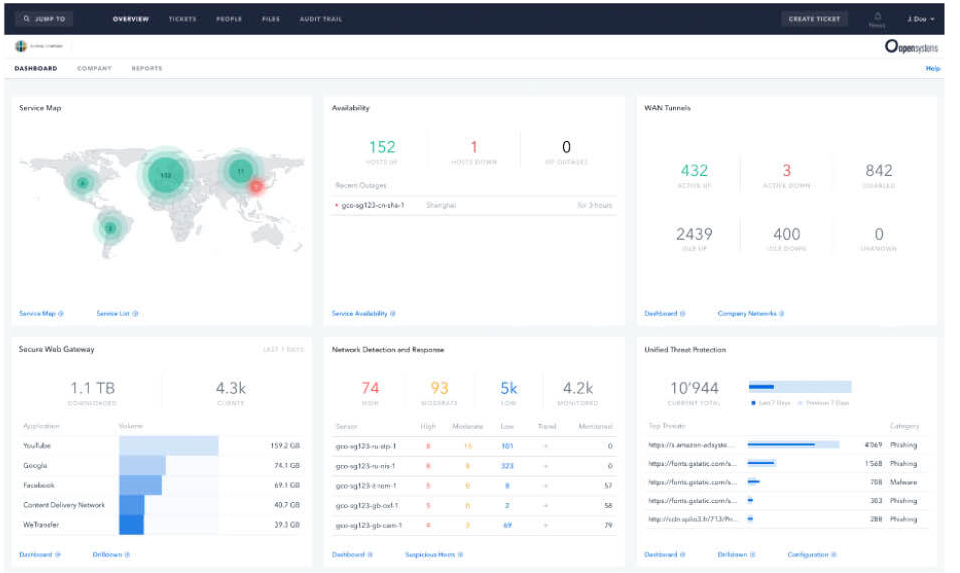
Was ist Cloud Risk Assessment?
Businesses across the globe complied with stay-at-home orders caused by the pandemic. As millions of people worked from home, cloud adoption soared.
For most businesses, the pandemic was unexpected, as was their rapid migration to cloud services. There was little time to perform research and implement policies for cloud applications. Less focus was given to perfection, and more emphasis was placed on time to production. Operational practices and policies, such as ensuring cybersecurity, weren’t perfect. They were ‘good enough.’

Thanks to an army of cybercriminals, cyber-attacks on cloud environments have risen six-fold since the beginning of 2020.
They use various new techniques and technologies to threaten cloud environments. Most cybercriminals conduct attacks in hopes of achieving financial gains. Others are state-sponsored actors or involved in corporate espionage. Some threats are a nuisance, while others do significant damage. Business losses include productivity, capital assets, confidential data, opportunity, and an organization’s reputation.
The cloud environment is continually evolving. As existing threats are halted, new vulnerabilities are exposed, and additional attacks are started.

Laden Sie unser eBook herunter. Dieser neue Ansatz für die Vernetzung umfasst eine Reihe von vollständig integrierten, über die Cloud verwalteten Security-Services, die vor Ort oder in der Cloud mit zentral verwalteter Sicherheit bereitgestellt werden. Erfahren Sie, wie Sie:
- Verringerung der Komplexität und des betrieblichen Aufwands
- Benutzerfreundlichkeit / Transparenz für Anwender
- Mehr Sicherheit durch einen Zero-Trust-Netzwerkzugriff

Cloud Vulnerabilities and Threats
There are many categories of vulnerabilities and threats associated with cloud environments. They include data breaches, insufficient access management, weak control planes, and insider threats.
- Attackers may gain access to the actual access control management system and create false access privileges.
- Credential confirmation management can be overwhelmed with a form of denial of service attack causing the system to halt and leaving users without access to their cloud applications.
- Faulty and vulnerable access control processes result in the need to re-issue credentials, which can be expensive and time-consuming.
Data Breaches
>A data breach is the unauthorized review, release, duplication, or transition of confidential information. The breach can be intentional or unintentional and includes private customer information, login credentials, radiology images, financial records, or engineering drawings and code. Anything that is deemed confidential or governed by compliance regulations like HIPAA and GDPR must remain secure and can only be accessed by authorized users. According to the nonprofit consumer organization ‘Privacy Rights Clearinghouse,’ tens of millions of unauthorized confidential files are released every year. A data breach also includes the improper disposal of equipment or data storage media that may contain confidential information. In many cases, a company must disclose a security breach to its customers and be liable for damages.
Insufficient Access Management
>Identity management controls access to sensitive applications and information. Nearly all businesses have some form of access management. It’s important that these systems remain fluid. Customers, users, employees, and business partners come and go or change positions. When possible, the system should unify access control under one umbrella. Changes to access should be unilaterally executed on all cloud applications eliminating the possibility of forgetting a seldom-used application. In many cases, access management policies and procedures must be documented and demonstrable. This is to ensure they don’t pose a risk to cyber-attacks and meet regulatory compliance requirements. The systems themselves must also be hardened to prevent attacks.
Weak Control Planes
>In any network, there is generally a data plane and control plane. The data plane is where the actual traffic travels. The control plane is where the instructions to the network travel. It manages all the devices, tools, sensors, gateways, firewalls, routers, switches, etc. The control plane is heavily used in software-defined architectures where devices constantly communicate and are often reconfigured by the software platform. A cybersecurity stack should include provisions for protecting the control plane by authenticating the source of communication between devices and the software management layer.
Insider Threats
>An insider threat and attack are when an employee, contractor, or other authorized individuals willingly harms or commits cybercrimes such a data theft, data destruction, malware introduction, security system reconfiguration, or changes in access policies and credentials. If the individual is knowledgeable of cybersecurity technologies, threats may go undetected for a long period. Other than proper initial and continuous screening, the best safeguard is creating a cybersecurity stack with independent checks and balances. When architecting a complete cybersecurity posture, it is important to consider insider threats and construct the stack accordingly.
A data breach is the unauthorized review, release, duplication, or transition of confidential information. The breach can be intentional or unintentional and includes private customer information, login credentials, radiology images, financial records, or engineering drawings and code. Anything that is deemed confidential or governed by compliance regulations like HIPAA and GDPR must remain secure and can only be accessed by authorized users. According to the nonprofit consumer organization ‘Privacy Rights Clearinghouse,’ tens of millions of unauthorized confidential files are released every year. A data breach also includes the improper disposal of equipment or data storage media that may contain confidential information. In many cases, a company must disclose a security breach to its customers and be liable for damages.
Identity management controls access to sensitive applications and information. Nearly all businesses have some form of access management. It’s important that these systems remain fluid. Customers, users, employees, and business partners come and go or change positions. When possible, the system should unify access control under one umbrella. Changes to access should be unilaterally executed on all cloud applications eliminating the possibility of forgetting a seldom-used application. In many cases, access management policies and procedures must be documented and demonstrable. This is to ensure they don’t pose a risk to cyber-attacks and meet regulatory compliance requirements. The systems themselves must also be hardened to prevent attacks.
- Attackers may gain access to the actual access control management system and create false access privileges.
- Credential confirmation management can be overwhelmed with a form of denial of service attack causing the system to halt and leaving users without access to their cloud applications.
- Faulty and vulnerable access control processes result in the need to re-issue credentials, which can be expensive and time-consuming.
In any network, there is generally a data plane and control plane. The data plane is where the actual traffic travels. The control plane is where the instructions to the network travel. It manages all the devices, tools, sensors, gateways, firewalls, routers, switches, etc. The control plane is heavily used in software-defined architectures where devices constantly communicate and are often reconfigured by the software platform. A cybersecurity stack should include provisions for protecting the control plane by authenticating the source of communication between devices and the software management layer.
An insider threat and attack are when an employee, contractor, or other authorized individuals willingly harms or commits cybercrimes such a data theft, data destruction, malware introduction, security system reconfiguration, or changes in access policies and credentials. If the individual is knowledgeable of cybersecurity technologies, threats may go undetected for a long period. Other than proper initial and continuous screening, the best safeguard is creating a cybersecurity stack with independent checks and balances. When architecting a complete cybersecurity posture, it is important to consider insider threats and construct the stack accordingly.
How Secure Is Your Cloud?
Cloud use, cybersecurity, and threats are continually evolving and may be unfamiliar to some IT professionals. Many businesses have found it worthwhile to obtain a cloud security risk assessment from a company experienced in identifying vulnerabilities and providing ‘hands-on’ cybersecurity solutions.
Contact our customer advocates to obtain a free assessment. Learn more about implementing a complete cybersecurity posture with MDR (Managed Detection and Response) or SASE (Secure Access Service Edge).